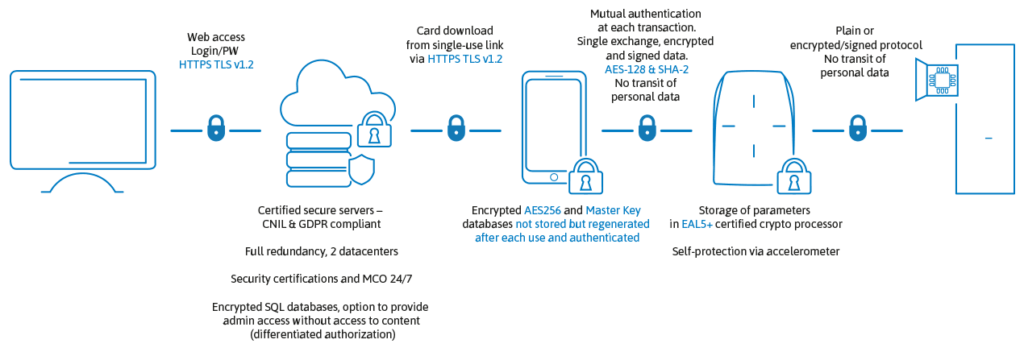
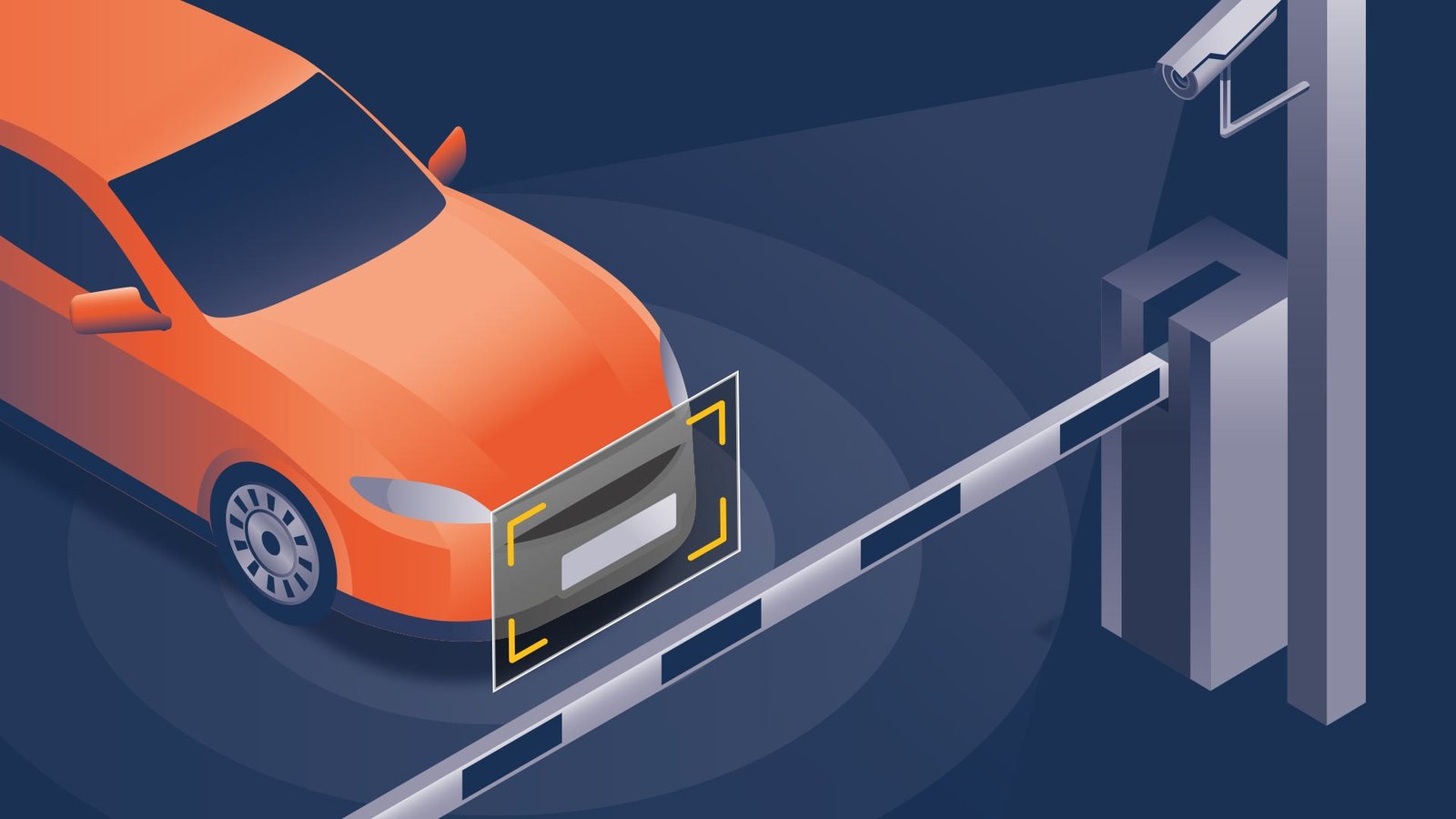
BLE, short for Bluetooth Low Energy, is the newest technology for keyless entry and access control credentials through mobile and smart phones.

How does Bluetooth and BLE access control work?
Bluetooth and BLE access control work by using a mobile device as a credential to gain access to a secured area. When a user wants to gain access to a secured area, they simply need to present their mobile device, which has been registered with the access control system, at the entrance. The system will then verify the user’s credentials and grant access if they are authorized
Advantages of Bluetooth and BLE access control
Enhanced security: Bluetooth and BLE access control systems offer enhanced security compared to traditional access control systems. This is because mobile devices are much harder to duplicate than physical access cards.
Convenience: Bluetooth and BLE access control systems are more convenient than traditional access control systems as users do not need to carry around physical access cards.
Cost-effective: Bluetooth and BLE access control systems are cost-effective as they eliminate the need for physical access cards, which can be expensive to produce.
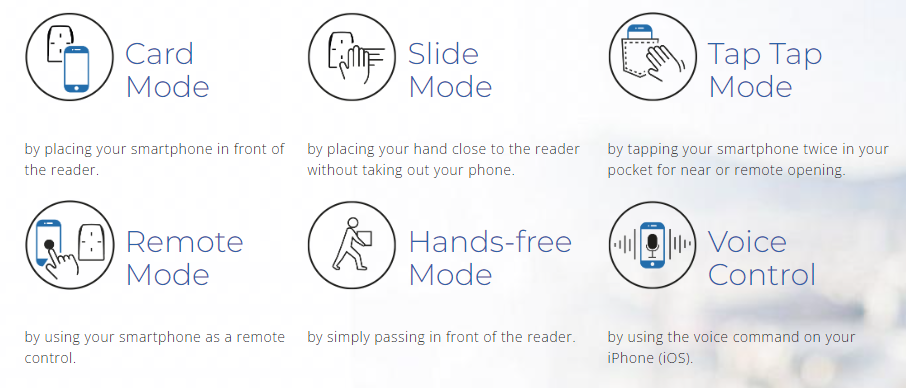
How to implement Bluetooth and BLE access control
Choose the right access control system: The first step in implementing Bluetooth and BLE access control is to choose the right access control system. There are many different types of access control systems available, so it is important to choose one that is compatible with Bluetooth and BLE technology.
Register mobile devices: The next step is to register mobile devices with the access control system. This involves pairing the mobile device with the access control system using Bluetooth or BLE technology.
Configure access rules: Once the mobile devices have been registered, access rules need to be configured. This involves setting up the access control system to grant or deny access based on specific criteria such as time of day or user role.
Test the system: The final step is to test the system to ensure that it is working correctly. This involves testing the system with different mobile devices and verifying that access is granted or denied based on the configured access rules.
Bluetooth and BLE access control systems offer enhanced security, convenience, and cost-effectiveness compared to traditional access control systems.
By choosing the right access control system, registering mobile devices, configuring access rules, and testing the system, you can implement a robust and reliable Bluetooth and BLE access control system in your home, office, or public place.
Bluetooth vs. Bluetooth Low Energy: What sets them apart?
Bluetooth and Bluetooth Low Energy have different applications. Bluetooth is capable of handling large amounts of data, but it drains battery life quickly and is more expensive. On the other hand, BLE is designed for applications that require less data exchange and can run on battery power for several years at a lower cost. The choice between the two depends on the specific goal of the intended use.
What is the reason behind the use of smartphones in access control systems?
Access control verifies a person’s identity using one or a combination of three main attributes:
– keypad authentication,
– RFID authentication,
– biometric contactless authentication.
Smartphones can utilize one or more of these authentication methods, with the phone’s credentials protected behind security features such as biometrics and PIN numbers. This allows for 2-factor access control verification once the authentication method is entered to access the phone.
Access to the Access Control credentials requires access to the phone first. Therefore, if the phone does not function, the Access Control credential will not work either. The credential works like any other app on the phone, requiring the phone to be turned on and unlocked for use.
The availability and built-in multi-factor verification are the primary reasons why organizations are interested in using smartphones for upcoming access control implementations. Additionally, the majority of people nowadays own and use a mobile device.
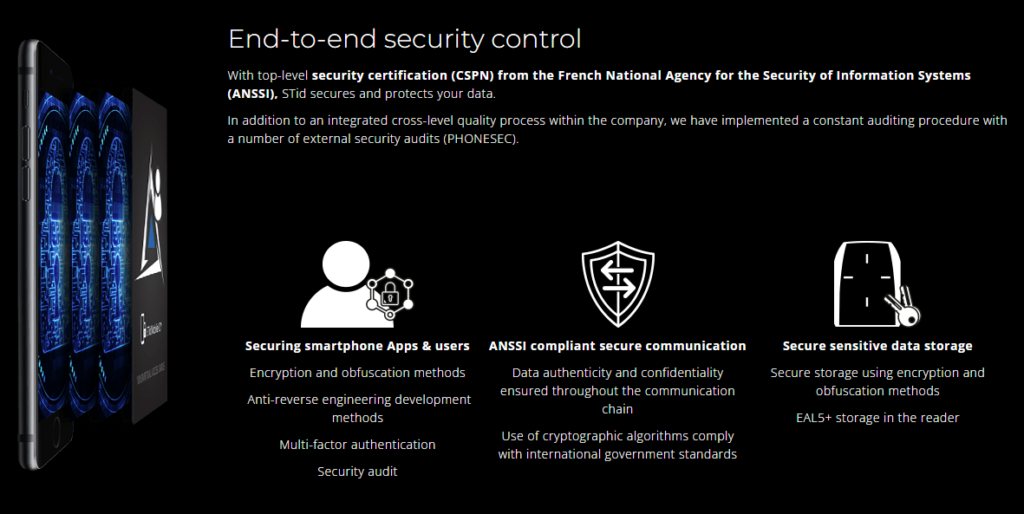
What are the benefits of using Bluetooth technology for access control systems?
Using Bluetooth technology in access control systems has several advantages.
Firstly, Bluetooth readers have lower running costs compared to RFID readers, as the user’s smartphone serves as the authentication device, eliminating the need to supply and deliver RFID cards, key fobs, etc.
Secondly, Bluetooth Low Energy is highly efficient and can significantly extend the battery life of smartphones compared to standard Bluetooth.
Thirdly, Bluetooth’s read range can be adjusted from an inch to over 15 feet, allowing for customizable read ranges for different applications. For instance, installers could set up a reader requiring a one-meter range at the front door, while providing a longer read range of around six feet for entering the facility gate, ensuring that users do not need to lean out of their car window to reach the reader.
Understanding Bluetooth Technology and Its Functionality
Bluetooth is a wireless technology that allows data exchange between devices over short distances using UHF radio waves.
Bluetooth connections are limited to two devices and can transmit data over a maximum distance of 164 feet.
This technology is found in a wide range of products, including but not limited to:
Smart phones
Laptops
Speakers
Headsets/Headphones

Can the Security of Bluetooth Technology be Trusted?
Bluetooth technology is considered more secure than Wi-Fi, but its security can become unreliable if the security of the devices is not kept up to date. This involves regularly updating the phone firmware and laptop operating systems to ensure they are secure.
To enhance security, it is recommended to turn off Bluetooth when not in use and limit app permissions for Bluetooth. Maintaining distance can also help as most security attacks can only be carried out at close range.
Therefore, it is important to be aware of surroundings when using Bluetooth.
It is worth noting that Bluetooth attacks/hacking are relatively rare.
Find more in the following article “MISCONCEPTION 2: PERSONAL DATA IN MOBILE ACCESS”